Category: Cyber Security
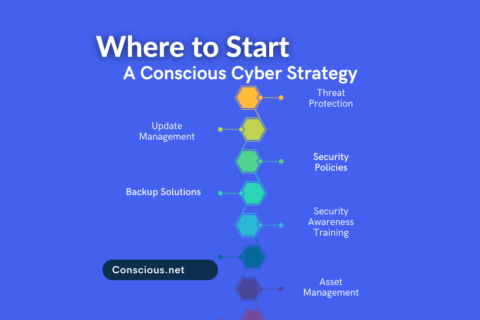
Are you struggling with how to protect your business from cyber threats? A strategic approach to cyber helps businesses create a plan to protect…
In the fast-paced realm of technology, where innovation is constant, businesses leverage cutting-edge solutions to stay competitive. However,…
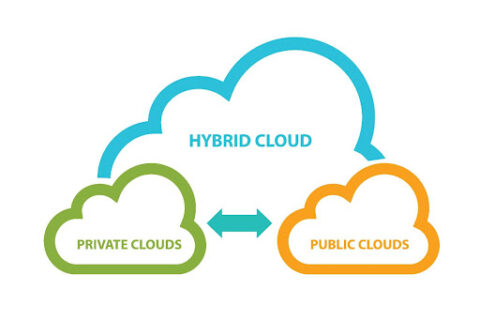
More and more businesses are utilizing cloud services to create better user experiences, store and share business data, and create more…
No matter the size of your business or organization, your employees are likely connected to your business through multiple devices. These devices…
Businesses have to prioritize the safety of data. Protected business information, customer details, and sensitive information are targets for bad…
In the fast-evolving landscape of technology, medium sized businesses and enterprises face an increasing array of cyber threats that can…
Today’s businesses are constantly adapting to grow their businesses but how quickly is your business adapting to cyber threats? Traditional…
It may seem strange now, but the concept of cloud computing was very unpopular when it first surfaced. People had fears and doubts about the safety,…
As businesses continue to navigate the dynamic landscape of cybersecurity threats, it becomes imperative to establish a robust defense against…
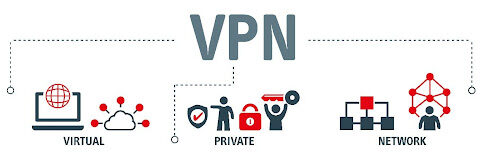
VPNs are the most effective way to browse online safely, securely, and privately. Unfortunately, the threats to our online freedom and privacy are…