Category: Endpoint Security
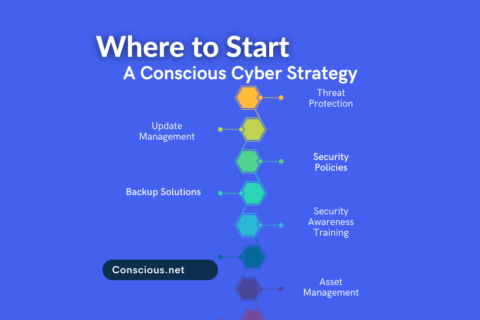
Are you struggling with how to protect your business from cyber threats? A strategic approach to cyber helps businesses create a plan to protect…
No matter the size of your business or organization, your employees are likely connected to your business through multiple devices. These devices…
Businesses have to prioritize the safety of data. Protected business information, customer details, and sensitive information are targets for bad…
Today’s businesses are constantly adapting to grow their businesses but how quickly is your business adapting to cyber threats? Traditional…
An information security policy is the foundation of a company’s security program. It defines the rules and processes and establishes standard…
Do you own a business? Are you juggling technology issues like email, phones, and most of all protection of your data? Do you have a privacy…
In today’s technology driven world, the average user has over 100 passwords to remember and many people save or store their passwords in some of…
Cyber threats such as ransomware and malware are at an all-time high. Companies have most of their data online and more employees working remotely…
Protecting data is a moral and legal obligation for most businesses today. Sensitive data such as personally identifiable information (PII),…
Data archiving, also known as EIA (Enterprise Information Archiving), is the process of creating long-term archives of all organizational data. Data…