News & Resources
Technology has become an integral part of the modern business landscape, enabling organizations to automate processes, improve productivity, and stay…
When you’re running your business, you may be relying on internal staff or an outsourced provider to help make the right recommendations for…
The role of the Chief Financial Officer (CFO) and Chief Information Officer (CIO) has never been more critical in today’s digital age. While these…
As businesses become increasingly reliant on technology, the role of Information Technology (IT) in driving financial performance has never been more…
We’re all in the cloud. Our information, our data, our credentials, they’re all cloud-based. If you’re a business owner, you are most likely…
Since the pandemic began in 2020, many organizations have had to adapt quickly to rapidly changing work environments coupled with new technologies. …
Of the many buzzwords, catchphrases and trending terms floating around the technology industry, the Metaverse and Web3 have got to be in the top 5. …
IT Alert: Patch Now!
Apple announced a security hole flaw (aka virus, spyware or malware) in it’s WebKit component that’s described as “Processing…
Since 2020, many businesses have rolled out massive technology. New platforms, new processes, and more automation have been some of the most common…
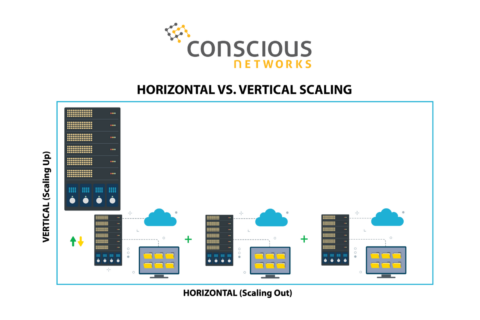
When your business is focused on growth initiatives, your technology is going to need to be scalable, to accommodate that growth. Scaling…